The energy sector is experiencing a massive digital transformation. This process is revolutionizing energy production, transmission, storage and consumption. Energy infrastructures are complex systems and, according to the U.S. Department of Homeland security, not only are the energy and chemical sectors vital in providing critical services to the U.S. population, but they are also part of the direct supply chain for every other critical industry, such as food, agriculture and emergency services.
The energy sector has always been an attractive target for threats. Intentional threats, such as cyber adversaries, ecoterrorists and vandals, have been in existence for decades. Other unintended but dangerous threats can include poorly trained staff and uninformed decision-makers that introduce risk into operations and the business. Many, if not most, energy operations rely on several different business units to refine, generate, transmit and distribute energy and resources. Experience proves that a structure full of diverse technology, geographic separation, and operational inconsistencies in an energy-focused operation can make it extremely difficult to ensure the network’s overall security.
The U.S. Department of Energy deems cybersecurity in the energy sector “one of the nation’s most important and complex national security challenges,” with energy infrastructure “a key target for adversaries.”
In late 2020 and throughout 2021, we became painfully aware that threats can be successful, whether sophisticated or simple. Lacking some basic security measures can result in severe consequences. From the bombing outside the Nashville AT&T center to the SolarWinds incident to Colonial Pipeline, the infrastructure vital to the U.S. remains a large target for attack.
Because of these events, significant changes were introduced in 2021, particularly with an increased federal role. This included several new Transportation Security Administration (TSA) security directives for pipelines, Federal Energy Regulatory Commission (FERC) orders, and initiatives stemming from the White House. At the same time, operators are facing other significant challenges, such as drastic market changes and the need to adapt to COVID-19. Regardless how the energy sector evolves, the threats posed on the energy market will continue to progress and seek new targets.
This can be overwhelming for operators and create cascading issues. For some operators, tackling security seems insurmountable; therefore, many organizations will simply accept the operational risks – an unnecessarily dangerous approach. Protection does not need to be daunting or costly but rather strategic and well-planned. It requires a blueprint and prioritization of the most critical operational aspects of the organization.
One hundred percent of the time, asset owners and executives will agree that, above all, the safety of their workforce and the public is the fundamental consideration when contemplating safety measures that work hand in hand with the continuity of operations and product delivery.
Approach
The rapid transformation of the energy system is well underway, driven by the need to expand access to secure energy and enabled by budding innovative technical solutions. In the most fundamental sense, technological innovation is seen as an enabler of progress; however, the exponential growth increases the levels of indiscriminate and targeted cyber attacks. As a result, energy companies are aggressively developing strategies to combat their security deficiencies and boost the protection of their digital assets.
Companies can significantly reduce cyber-related risks by using a strategic and structured approach that applies communication, organizational and process frameworks. To address the vast geographic, structural, and technical gaps in their networks and visibility, operators must take an integrated and layered approach to security.
Integration and transparent internal processes across teams are critical to up-, mid- and downstream operating spaces, where technology is diverse. Defining and structuring a process to enable clear, rapid communications can serve as the linchpins of these capabilities and processes, ensuring immediate information sharing, and marshaling the response to specific events.
Throughout the entire organization, companies must integrate cyber and physical security into their cultures. From the CEO down, teams must hear consistent, aligned messages stressing that security is everyone’s responsibility and emphasizing specific tactical actions needed as individual threats arise. In 2020, Stanford University professor Jeff Hancock and security company Tessian determined that 88 percent of data breaches are caused by employee error. It is impossible to achieve a good security position without considering all factors. Operations need physical assets and digital capabilities to remain secure and human interaction is perhaps the most critical consideration.
Implementation
Going beyond addressing the basics of securing the traditional IT and OT environments, cybersecurity must also consider the vast complexities of IoT, integrate innovative digital processes, such as automation, blockchain and artificial intelligence. Put simply, security measures must be woven into every facet of the operations.
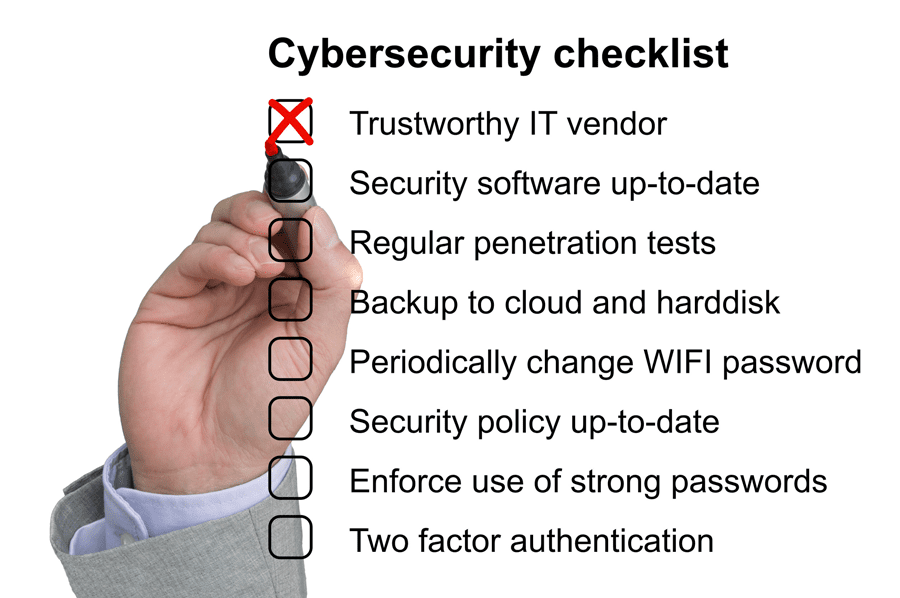
Here are some key points to consider when implementing a solid cybersecurity outfit in oil and gas:
- Planning – Develop a strategic plan that aligns with the organization’s foundation. Establish unwavering, clear policies and procedures. Define a security culture for the organization with the expectation and view that it is as important as operational safety.
- Prioritize critical assets, sites and operations – Return on investment is the holy grail for the majority of businesses. Defining these priorities allows money to be spent on areas with the most ROI.
- Understand threat, but don’t fixate on it – Threats are everywhere and will always be prevalent. They can present in the form of cyber adversaries, extreme weather events and unintentional threats, such as inadequately trained staff. Developing security regimens should focus on creating defense in depth with various layers of overlapping cybersecurity controls.
- Identify vulnerabilities to your operations and take steps to reduce them – It’s impossible to achieve zero vulnerabilities, but weaknesses that can be exploited can be reduced. By continually refining constraints within the system of operations, new requirements are identified to support security for the overall system, and steps can be taken to enforce adherence through system design, processes and procedures, and social controls.
- Training – Human error is one of the most significant risks to cybersecurity and can be prevented through training. Strengthen the workforce’s capabilities and drive an increase in overall threat awareness. Empower employees with the skills needed to defend and protect the security of our energy systems by providing the tools and resources to mitigate them accordingly. Regularly prepare for threats and continue to drill in on processes.
- Maintain security – Many owners/operators fall into the “set it and forget it” mentality. Protection requires consistency and reevaluation, and should involve regular patches of digital assets, keeping data secure, and surveying sites. Ongoing reevaluation of security to ensure it aligns with organizational goals.
- Preparedness is crucial. It creates resilience in operations to prevent and prevail through incidents without disruption or cost. Inaction can be costly. Consequences can be tangible, such as damage, injury or a complete standstill of operations. However, even more daunting, the loss of shareholder confidence and reputation damage can have long-lasting detrimental effects. It is much better to be prepared now than attempt to clean up the damage later.
Maintaining Security
Security must be ingrained in the infrastructure and overall operating strategy. Just like safety in our most vital sector, a lack of security in any working environment can have serious consequences. Cyber or physical attacks often reach a level of success because of a lack of simple protections, processes or awareness. Even small and simple changes, such as changing a daily operating procedure, can add tremendous value in securing operations.
Increased federal oversight in the operations of the energy sector security has added new compliance requirements, which will be the new norm. It is safe to anticipate that additional required security layers will continue to roll in over the coming years. Compliance is essential, and in today’s atmosphere, most operators in the up-, mid- or downstream space have some level of security plan in place and are working on illustrating their due diligence in protecting assets, data, sites and staff. Maintaining and testing those plans is equally important to ensure the desired security position is maintained.
Annie McIntyre is an expert in operational security for critical infrastructure and the director of operational security for EverLine. Everline’s technical stack offers fully integrated compliance, SCADA/IT, control room and security services. Visit EverLine at www.everlineus.com.
Oil and gas operations are commonly found in remote locations far from company headquarters. Now, it's possible to monitor pump operations, collate and analyze seismic data, and track employees around the world from almost anywhere. Whether employees are in the office or in the field, the internet and related applications enable a greater multidirectional flow of information – and control – than ever before.